Fail2Ban Port 80 to protect sites from DOS Attacks
FAIL2BAN Port 80 is used to protect sites from DOS Attacks. Fail2ban scans log files (e.g. /var/log/apache/error_log) and bans IPs that show the malicious signs — too many password failures, seeking for exploits, etc. Generally Fail2Ban is then used to update firewall rules to reject the IP addresses for a specified amount of time, although any arbitrary other action (e.g. sending an email) could also be configured.
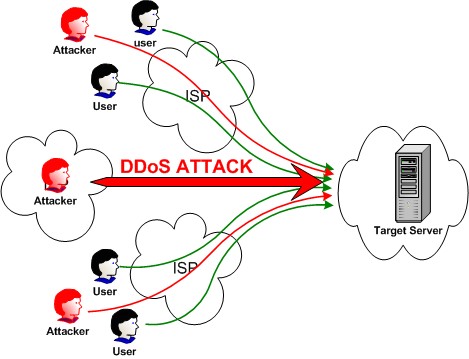
In computing, a denial-of-service (DoS) or distributed denial-of-service (DDoS) attack is an attempt to make a machine or network resource unavailable to its intended users. The machine or network is flooded with useless traffic in this attack.
To protect your website or service, Fail2Ban can be used on different ports. Here it will be explained how to use Fail2Ban on port 80. You can also check HOW TO USE FAIL2BAN ON PORT 22.
Installing Fail2Ban on Ubuntu 14.04
We’ll also grab iptables-persistent to allow the server to automatically set up our firewall rules at boot. Fail2Ban can be installed using the following two commands on terminal:
sudo apt-get update sudo apt-get install iptables-persistent fail2ban sendemail
Configuring Fail2Ban with Service Settings
Fail2Ban keeps its configuration files in /etc/fail2ban folder. The configuration file is jail.conf which is present in this directory. This file can be modified by package upgrades so we will keep a copy of it jail.local and edit it.
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local sudo vim /etc/fail2ban.local
There are different sections in Fail2Ban configuration files. The [DEFAULT] section is applied to all services enabled for fail2ban. If you want to ignore some particular ips by Fail2ban then you can enter it in the ignoreip section.
ignoreip=127.0.0.1/8
Bantime is the time for which the ip is banned by fail2ban. Findtime is the time for which the ips will be observed. Maxtry is the maximum try which will be given before blocking. These all resembles to a general situation of logging in online-banking in which after some insuccessful attempts you are blocked for a day.
Configuring mail settings in Fail2Ban
The mail settings are used to send an email whenever an ip is blocked by Fail2Ban. The mail settings can be configured by modifying the following variables:
destemail = fail2ban@localhost sendername = Fail2Ban_user mta = sendmail
The destemail must be set to the email-address at which the email is wish to be received. The sendername is set to Fail2Ban by default. The mta is the agent which you will use to send email. The other mta could be sendemail etc.
If you would like to configure email alerts, you can change the value from action_ to action_mw. If you want the email to include the relevant log lines, you can change it to action_mwl. Make sure you have the appropriate mail settings configured if you choose to use mail alerts.
Configuring Fail2Ban for Apache/Nginx Web Server
To configure for Apache/Nginx, edit the apache/nginx section. The Apache section can be modified as :
enabled = true port = http,https filter = apache-auth logpath = /var/log/apache*/*error.log maxretry = 6
The apache/nginx section can be modified according to the needs.
Restarting Fail2Ban service
sudo service fail2ban stop sudo service fail2ban start
Now you are done. The fail2ban has been implemented. Try to logging in using invalid credentials . The ip will be blocked after some number of attempts and you will receive an email from fail2ban service.





Pingback: Block admin login page attack using Fail2ban | TO THE NEW Blog
Pingback: Preventing Brute Force attacks due to OpenSSH Vulnerability (MaxAuthTries bypass) | TO THE NEW Blog
Nice article Mohit… It helped me a lot
.