Auditing Your Ubuntu Servers
You might be wondering how to audit your Ubuntu server / your Ubuntu local machine. Well, In this blog I will show you how easy it is do so. Auditing can be done by many ways of which few we shall discuss here. There are 3 following scenarios which we will be discussing :-
1.Finding from where logins are done & commands are executed
We can find the IP from where a ssh login has been done and commands have been executed. Also we can get the status of logins & those commands.
Suppose a Server has 2 users :-
1. Ubuntu which has sudo access.
2. ranvijay is a another user created by useradd.
(password login to server has been enabled)
Login to your server using Ubuntu user.
Also, login to server in with user ranvijay from another machine which might be running on the same or other network.
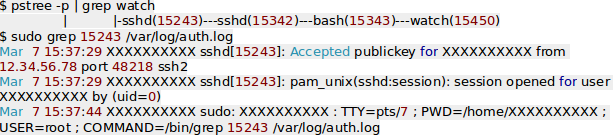
Now, if we want to check from where the ssh logins have been made
Run command ->
“pstree -p” and grep whatever command you want to audit
like “grep sshd”
or simply “ps -ef | grep sshd”
This will return PIDs of ssh logins which have been processed till now.
Logs are stored in auth.log file
So,
“sudo grep 2448 /var/log/auth.log” ( 2248 is the process ID & it may vary in your server)
After running the above command, multiple PIDs will be shown, so you can filter the output according to your use.
You would get a similar output :-
2.For finding who changed / executed a particular file /process /system calls
For this, we have the auditd tool
Install it by using the following command.
“apt-get install auditd audispd-plugins”
Auditd works on some user defined rules. So, now we have to set the rules.
These rules specify for which file to & the operations on the file to keep track of
Now run command ->
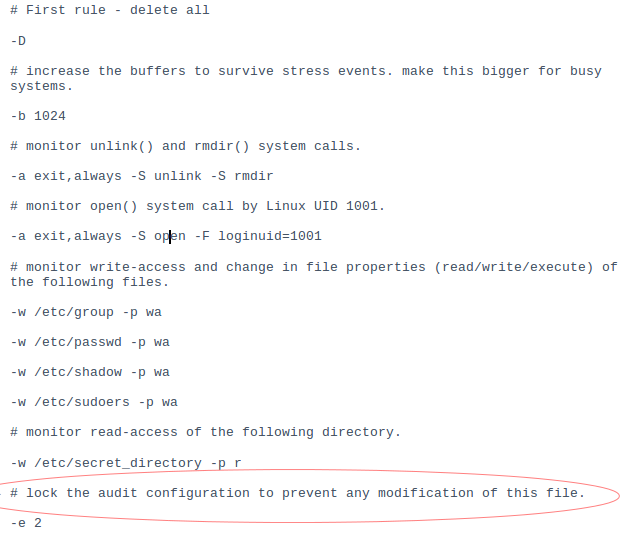
“vim /etc/audit/audit.rules”
Here write rules like below :-
Note:- When you write the line highlighted you wont be able to edit the audit.rules file again. There is an alternative to you opening the file and editing it. If you don’t want to edit the file you can directly define rules via command.
“auditctl -a exit,always -F path=/etc/passwd -F perm=wa”
This will append audit.rules file & activate audit on passwd file.
A Few more auditctl commands:-
To see all system calls made by a program:
“auditctl -a entry,always -S all -F pid=1005”
To see files opened by a specific user:
“auditctl -a exit,always -S open -F auid=510”
To see unsuccessful open call’s:
“auditctl -a exit,always -S open -F success!=0”
Here are a few switches :-
r = read
w = write
x = execute
a = attribute change
Restart the service.
“sudo service auditd restart”
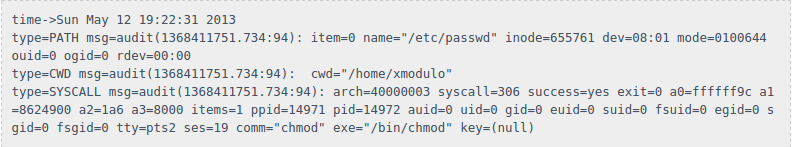
Now, run the below command with the file you want to edit.
“ausearch -f /etc/passwd”
This will audit file passwd and return results.
3. Now auditing User actions ( Who What ,How Much & When)
For this, we need to Install acct
“sudo apt-get install acct”
This gives many commands few of which are :-
ac : ac command prints the statistics of user logins/logouts (connect time) in hours.
ac -d : Using command “ac -d” will prints out the total login time in hours by day-wise.
ac ranvijay : To get the total login statistics time of user “ranvijay” in hours, use the command as.
sa -c : The command “sa -c” displays the highest memory percentage usage of users.
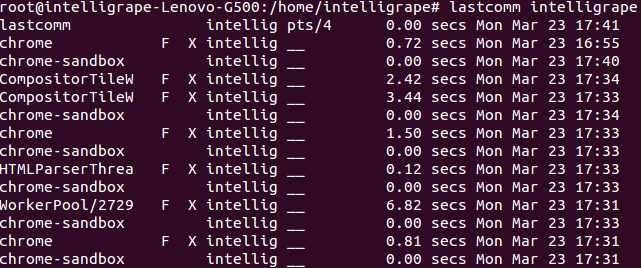
lastcomm : The “lastcomm” command is used to search and display previously executed user commands information. You can also search commands executed by individual usernames.
Run command ->
“lastcomm username”
or you can find which user ran a particular command & when
“lastcomm ls“or “lastcomm rm”
All this will really help you keep track of the users, keep your server safe & let you know who is responsible for which action.